Shisui - Fword CTF 2021 Write-up
Table of Contents
tl;dr
- XSS using DOM Clobbering
<a id="showInfos"></a><a id="SETTINGS" name=check data-timezone="aaa" data-location="eval(window.name)"><a id="SETTINGS" name="x">- Bypass CSRF protection to execute XSS and read flag.
No. Of Solves: 5
Challenge points: 999
Source Code: here
#
Initial Analysis
We’re given a web application that has a login and register page. Upon registering, the user is presented with a feedback page.
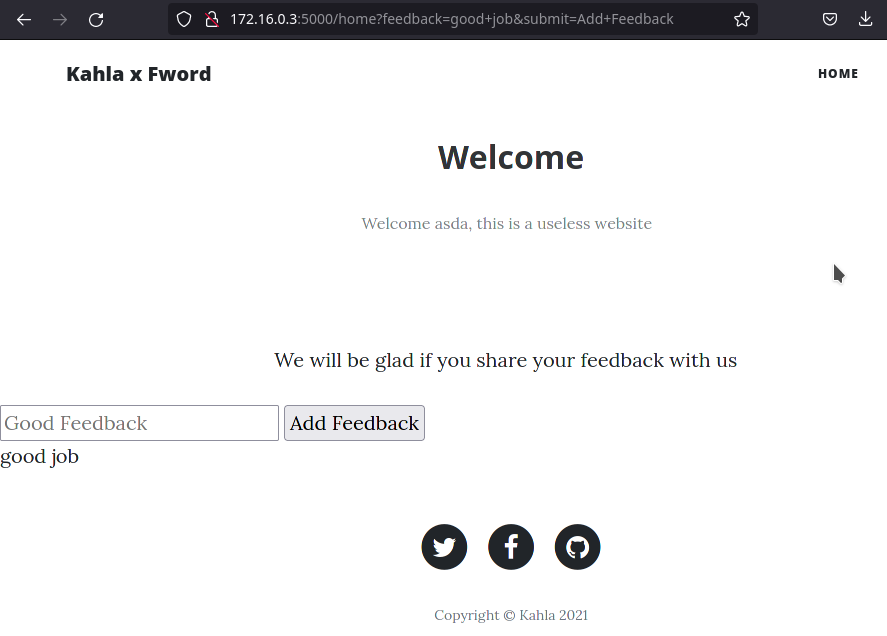
On inspecting the source code, one can see that the page uses latest version of DOMpurify and runs the below JavaScript code to display the comment.
| |
We are allowed to inject HTML but not JavaScript. We also have a main.js file with the following content.
| |
The initial lines of the above code along with the HTML Injection that we have, can cause DOM Clobbering attack.
#
Exploit
##
Trigerring XSS
The looseJsonParse function can be used to trigger an XSS. However, it requires three conditions - window.showInfos && SETTINGS.check && SETTINGS[0].dataset.timezone.length>2.
window.showInfoscan be set by injecting<a id="showInfos"></a>.The second condition can be bypassed by clobbering
window.SETTINGS.
| |
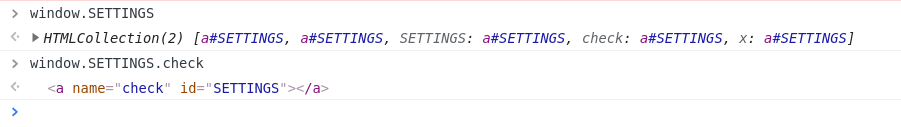
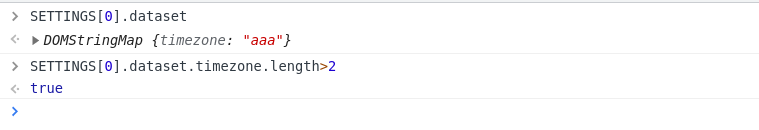
- For the third condition, we require
SETTINGS[0].dataset.timezone.length>2. This can be solved by setting data attribute to the HTML tag. (Read about dataset attribute here.)
| |
Combining all the conditions, our payload becomes,
| |
With the above payload, window.name will be executed by JavaScript. Now we can execute JavaScript by sending the admin to a page containing the below script.
| |
Now, we have an authenticated XSS. But the admin bot does not authenticate on submitting a URL.
##
Delivering Exploit
Create a subdomain (say challenge.example.org) that has a CNAME record to shisui.fword.tech (challenge server). Then on the main domain, we set a cookie to authenticate the admin bot.
The exploit script that runs on the main domain:
| |
#
Flag
| |